Nǐ hǎo péngyǒu.
Last L2 protocol post. Wont be a long one, not too much to it. Let’s dive straight in…
UniDirectional Link Detection (UDLD) is a protocol designed to detect (you guessed it) unidirectional links. So what do we mean by unidirectional links? A link in which data is only transmitted one way. I should probably mention this protocol is only for fibre links. As we know with fibre links, there are 2 connectors, a transmit and receive. If one of those fail, this can cause major problems with spanning tree and loop detection. Therefore, UDLD is there to safeguard against this. And as its only for fibre links, UDLD is only enabled on SFP ports.
So how does it work? It works by sending UDLD packets that include the system ID and the port ID of the interface transmitting the packet. The neighbour device then returns in kind with its own info, an acknowledgement if you will. It’s essentially a keepalive mechanism. UDLD has 2 modes: Normal mode (passive) and aggressive (active). In normal mode, if a frame is not acknowledged, the link is ‘undetermined’ yet the port remains active. In aggressive mode, when a frame is not acknowledged the switch sends another 8 packets, 1 per second. If none of these are acknowledged, the port goes into err-disabled mode and stops forwarding traffic, thereby eliminating any potential STP loops. USEFUL MODE. Let’s have a gander at the syntax:
To enable UDLD globally (this will only take effect in SFP ports), we use the UDLD enable/aggressive command as below:
We can then disable UDLD on SFP ports where required by using the UDLD disable command within an interface. So lets take a look at UDLD in action! Wait. I don’t have any fibre cables, nor can I simulate one… Tricky one to simulate a unidirectional link in a GNS3 lab, but where theres a will theres a way. UDLD uses a proprietary MAC address 00:10:0c:cc:cc:cc at L2 for traffic. If we can filter traffic to this MAC address coming IN on one interface, we might be able to simulate a unidirectional link failure. And how do we filter MAC addresses? MAC access-lists! Also in this case, as we’re not using SFP ports, we need to activate UDLD manually on a specific ethernet interface. So we’ll set up the MAC access-list and port configuration as below:
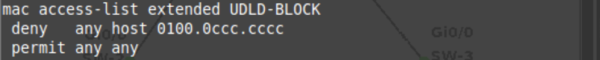
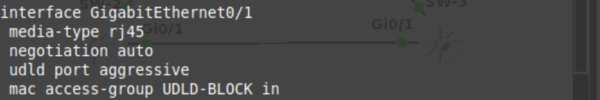
So we’ve now got the port blocking incoming UDLD traffic on the interface connected to the neighbouring switch. Lets take a look at some debug output after the 8 seconds of no UDLD acknowledgements:
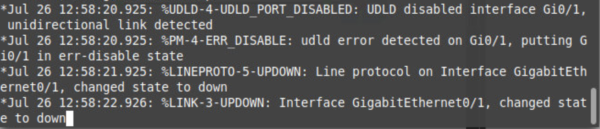
Once the issue causing unidirectional link has been sorted, the interface can be shut/no shut, or the UDLD reset command can be run from privileged exec mode. There we have it. UDLD. Tick.
Jack x

Leave A Comment